The Blog
The latest news and insights covering cyber security, threats, vulnerabilities, incident detection, regulatory compliance news and trends.
How to Secure Employees’ Home Wi-Fi Networks
How to Secure Employees' Home Wi-Fi NetworksBusinesses must ensure their remote workers' Wi-Fi networks don't risk exposing business data or secrets due to fixable vulnerabilities. Bert Kashyap CEO and Co-Founder at SecureW2 While we are close to seeing the light at...
Do You Have a DCIM Roadmap ?
Do You Have a DCIM Roadmap ?Prospective customers usually question our roadmap. Although that's a good question, it's difficult to answer not because I believe we have a 'roadmap problem' at Graphical Networks, but because explaining our reasoning and viewpoint behind...
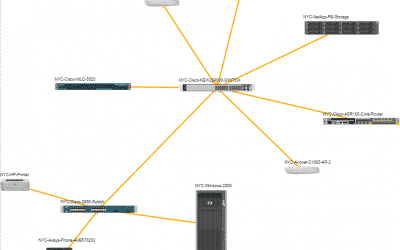
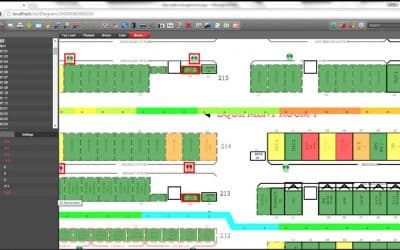
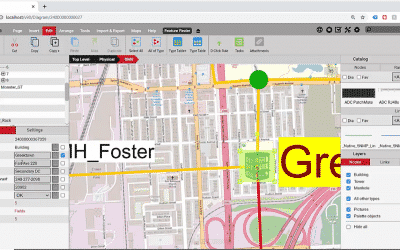
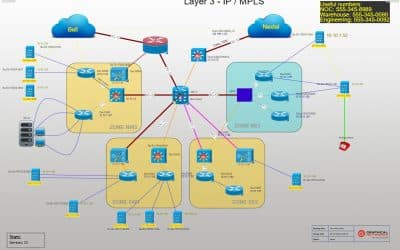
4 Use Cases: Logical Network Diagrams
4 Use Cases: Logical Network DiagramsLogical network diagrams can take many forms: they can be as simple as post-it notes on your desk, Visio diagrams, or up-to-date and pixel-perfect diagrams that describe your network in real-time (like the ones netTerrain...
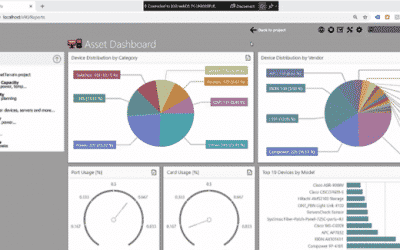
Design Your Own Dashboards in netTerrain DCIM
Design Your Own Dashboards in netTerrain DCIMHaving all of the network infrastructure documentation in one system isn't necessarily the goal: we also want to get insight from the data, learn more about how the data is aggregated, and maybe take action. Normally, these...
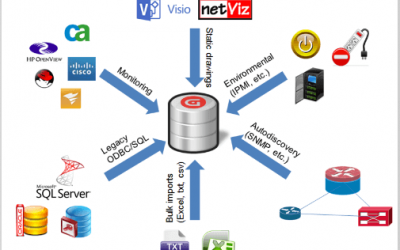
ROI for Network Documentation and DCIM Software
ROI for Network Documentation and DCIM SoftwareIn this blog series, we'll look at the return on investment (ROI) for network documentation and network mapping tools. We'll go over a numerical example in this article and the next one. Network mapping and documentation...
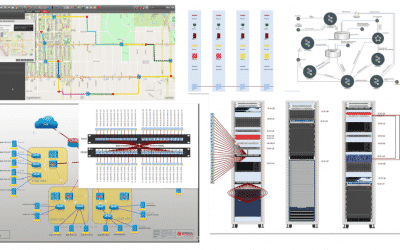
DCIM It’s All About Communication
DCIM It's All About CommunicationWe've said it too many times on this site over the years: no single piece of software can do everything. Yes, many companies are searching for a single pane of glass view — and with good reason: there are so many moving parts and...
netTerrain Mobile App and More
netTerrain Mobile App and MoreWelcome to netTerrain 9.0, a new year and a new edition! The arrival of 9.0 marks the end of our single-digit major release cycle and the start of the 9.x series, also known as "Europe" (as you'll note when you check in or look at the...
DCIM’s Impact on Data Center Efficiency
DCIM's Impact on Data Center EfficiencyWe've recently published a few articles about how Data Center Infrastructure Management (DCIM) software assists data centers in becoming more efficient, which got me thinking about where we started and where we are now .Do you...
Limited Custom Fields in DCIM Software ?
Limited Custom Fields in DCIM Software ?We've said it before, we'll say it again now, and we'll say it again later: successful DCIM software must be flexible. We'll look at some use scenarios in this blog (and video) to explain why it's crucial to have flexibility...
Network Documentation Calculating Your ROI
Network Documentation Calculating Your ROIIf you are having issues that you think will be solved with network documentation and network mapping software then this article is for you.A report on the positive effects network mapping software implementation has had with...
Questions Everyone Should Ask with a DCIM Demo
Questions Everyone Should Ask with a DCIM DemoDo your research before deciding on DCIM software for your organisation. Ask thoughtful inquiries and thoroughly assess a possible DCIM vendor. Why? Unfortunately, not all DCIM solutions are made equal, some products that...
What do you need with Network Documentation ?
What do you need with Network Documentation ?A Reddit comment about network documentation was given to me by one of my workers. What's useful for documentation software, inquired the original poster? "Don't buy that," a Redditor stated after mentioning a famous brand...
Difference Between Risk, Threat, and Vulnerability in Cyber Security
Difference Between Risk, Threat, and Vulnerability in Cyber Security Every industry has its own vernacular and the cyber security industry is no different. Cyber security professionals use precise terminologies to express and address a wide range of aspects. This...
We won’t spam!